
Posted on Saturday, Feb 25th, 2023
Upgrade Your Cyber Security with Blue Summit
Cyber security is more crucial than ever in today's digital world. With the increased use of technology and the internet, individuals and organizations must protect themselves against cyber-attacks. Cyber security service is intended to assist individuals and companies in protecting themselves from cyberattacks and ensuring the security of their data. This blog will go over cyber security services in depth.
Cyber Security Service - An Overview
Cyber security services are a set of practices and processes designed to protect an individual or organization's digital assets from cyber threats. These services encompass a wide range of solutions that aim to prevent, detect, and respond to cyber-attacks. The primary goal of cyber security services is to ensure that confidential information remains secure and that the business operations remain uninterrupted.Types of Cyber Security Service
1. Risk Assessment and Management
The process of discovering, analyzing, and evaluating threats to an organization's digital assets is known as risk assessment and management. This service analyses an organization's security posture in depth, finding potential weaknesses and making recommendations for remedy.2. Network Security
Network security is the process of protecting an organization's computer networks from unauthorized access, misuse, or modification. This service includes firewall installation, intrusion detection and prevention systems, and network monitoring.3. Cloud Security
Cloud security is the process of protecting an organization's data and applications that are hosted on cloud-based platforms. This service includes the deployment of security measures such as encryption, access control, and monitoring.4. Identity and Access Management
Identity and Access Management (IAM) is the process of managing digital identities and controlling access to digital resources. This service includes user authentication, authorization, and multi-factor authentication.5. Data Loss Prevention
Data loss prevention (DLP) is the process of protecting sensitive data from unauthorized access, loss, or theft. This service includes the deployment of data encryption, monitoring, and access control measures.6. Incident Response
Incident response is the process of responding to and managing a cyber-attack. This service includes identifying the nature and scope of the attack, containing the attack, and implementing remediation measures.7. Compliance and Regulatory Services
Compliance and regulatory services help organizations meet legal and regulatory requirements related to cyber security. This service includes compliance audits, security assessments, and security policy development.Advantages of Cyber Security Service
Blue Summit's USPs
1. Comprehensive and Customized Solutions
We give personalized solutions to our clients' individual demands. This requires a thorough awareness of the particular risks and difficulties that each company faces, as well as the capacity to develop and implement strategies that effectively handle those risks.2. Always Ahead
Our company's key ability is to stay ahead of emerging threats and trends in the constantly evolving field of cyber security. This requires ongoing investment in research and development, as well as our commitment to continuous learning and improvement.3. Proactive Approach
We take a proactive approach to cyber security and focus on prevention rather than just responding to threats after they occur. This also includes ongoing risk assessments, vulnerability testing, and regular security audits.4. Strong Customer Support
Providing excellent customer support is critical in the cyber security industry and we are always ahead of the line. We offer 24/7 support and rapid response times to customer inquiries and concerns.5. Reputation
Blue Summit’s reputation for reliability, trustworthiness, and responsiveness is a critical differentiator in the competitive cyber security market. Clients know that they can rely on us to be available and responsive when they need assistance, and that they can trust us to keep their sensitive information secure at all times.6. Expertise and Experience
One of the most important factors that differentiate cyber security service providers is the level of expertise and experience one has in the field. We have a team of highly skilled and experienced security professionals who have a proven track record of successfully protecting our clients' systems and data.We provide a very cost effective and flexible cyber security services for small businesses.
Overall, a combination of all these factors makes our company differentiate itself in the competitive cyber security industry and attract new customers.
In Short
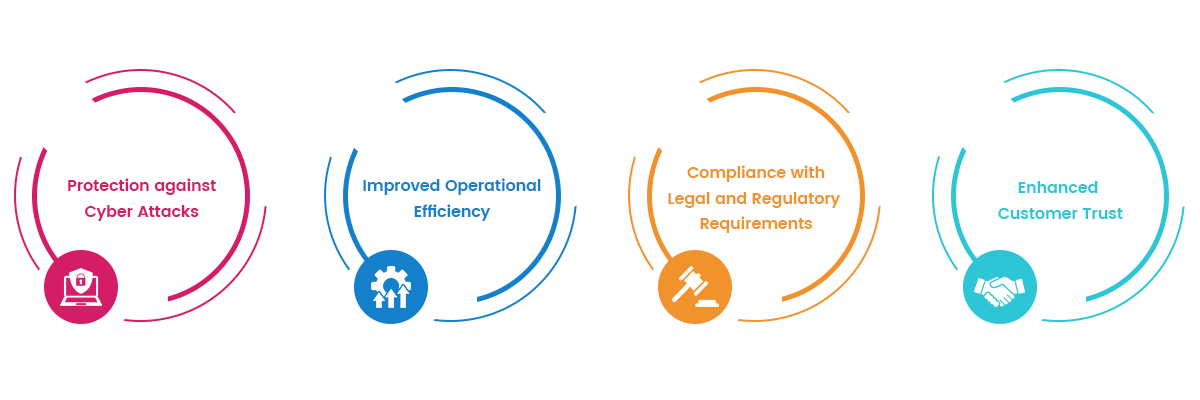
Cyber security services are essential for individuals and organizations to protect themselves against cyber threats. By investing in cyber security services, organizations can improve their operational efficiency, meet legal and regulatory requirements, and enhance customer trust.So if you are in search of a partner worthy of your time and investment, search nowhere else because we are right here.
Contact us now for free consultation on cyber security. Blue Summit has collaborated with OdiTek Solutions, a frontline custom software development company. It is trusted for its high service quality and delivery consistency. Visit our partner's page today and get your business streamlined.
REFER TO OTHER RELEVANT CONTENTS

iOS Development
The 4G revolution is rapidly taking hold. The days of requiring a desktop or cable connection to access the virtual world are long gone. Our lives are drastically changed by mobile devices and fourth-generation wireless communication standards, and no gadget dominates this concept more than...
read more







