
Posted on Thursday, Aug 24th, 2023
From Startups to Enterprises: Tailoring the NIST CSF Framework to Your Organization
In an era where cyber threats have become more sophisticated and pervasive, organizations of all sizes are realizing the importance of robust cybersecurity measures. The NIST (National Institute of Standards and Technology) Cybersecurity Framework has emerged as a versatile and comprehensive guide to help organizations strengthen their cybersecurity posture. From agile startups to sprawling enterprises, the NIST Framework offers a blueprint that can be tailored to fit the unique needs and challenges of any organization. In this blog, we will explore how businesses, regardless of their size, can effectively adopt and adapt the NIST Framework to enhance their cybersecurity defences.
Understanding the NIST Cybersecurity Framework
The NIST Cybersecurity Framework provides a structured approach to managing cybersecurity risk. It consists of five core functions: Identify, Protect, Detect, Respond, and Recover. These functions work together to create a holistic and proactive approach to cybersecurity.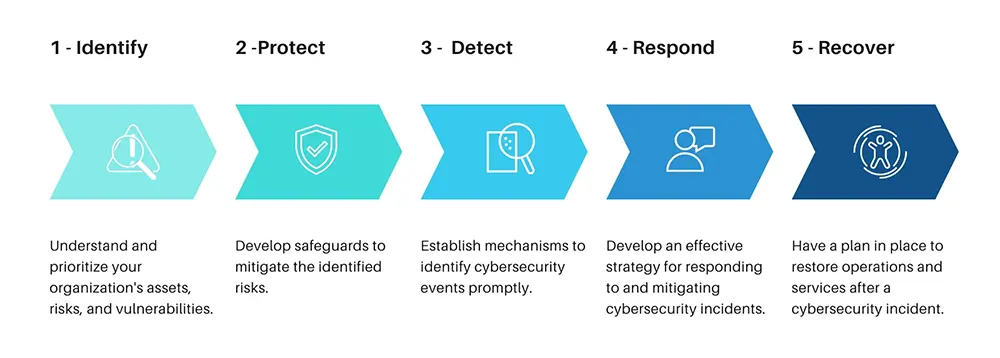
Identify: The "Identify" function focuses on understanding and managing cybersecurity risks to systems, assets, data, and capabilities. It involves developing a clear understanding of the organization's business context, its cybersecurity roles and responsibilities, and the potential risks it faces. This function helps organizations establish a foundation for effective cybersecurity risk management.
Protect: The "Protect" function involves developing and implementing safeguards to ensure the delivery of critical services and protect against threats. This includes measures to limit or control access to systems and data, training employees and partners in cybersecurity best practices, and implementing technologies and processes to safeguard data integrity and confidentiality.
Detect: The "Detect" function focuses on identifying the occurrence of cybersecurity events promptly. It involves implementing continuous monitoring, intrusion detection systems, and other mechanisms to quickly detect potential security breaches or anomalies. Detecting threats early is crucial for effective incident response.
Respond:The "Respond" function outlines the actions to be taken when a cybersecurity incident is detected. This includes having an incident response plan in place, setting up communication protocols, and coordinating with relevant stakeholders. The goal is to contain the incident, mitigate its impact, and restore normal operations as quickly as possible.
Recover: The "Recover" function involves developing and implementing strategies to restore systems and services after a cybersecurity incident. This includes restoring data from backups, ensuring systems are secure before bringing them back online, and learning from the incident to improve future response and recovery efforts.
NIST Cybersecurity Framework Controls
The NIST Cybersecurity Framework provides a set of recommended cybersecurity controls that organizations can implement to enhance their cybersecurity posture. These controls are organized within the framework's categories and subcategories, aligning with the five core functions: Identify, Protect, Detect, Respond, and Recover. Here are some examples of cybersecurity controls within each of these core functions:1. Identify
Asset Management:
Control: Identify and document assets, including hardware, software, and data, that support business operations and security requirements.Risk Assessment:
Control: Conduct regular risk assessments to identify and prioritize cybersecurity risks to the organization's systems, data, and capabilities.2. Protect
Access Control:
Control: Implement and enforce access controls based on the principle of least privilege to ensure that users have access only to the resources they need.Data Security:
Control: Apply encryption to sensitive data both at rest and during transmission to protect it from unauthorized access.3. Detect
Anomalies and Events:
Control: Implement automated mechanisms to detect unusual activities or behaviors that might indicate a cybersecurity incident or compromise.Security Continuous Monitoring:
Control: Continuously monitor the organization's systems and networks for security vulnerabilities, weaknesses, and suspicious activities.4. Respond
Response Planning:
Control: Develop an incident response plan that outlines the steps to be taken in the event of a cybersecurity incident, including communication, containment, eradication, and recovery.Analysis:
Control: Conduct a thorough analysis of the incident to understand its scope, impact, and root causes.5. Recover
Recovery Planning:
Control: Develop and maintain a plan for restoring critical systems and services in the aftermath of a cybersecurity incident.Improvements:
Control: After responding to an incident, analyze the organization's response efforts and identify areas for improvement to enhance future incident response capabilities.Tailoring the Framework for Startups
Startups often have limited resources and a need for agility. Here's how startups can adapt the NIST Framework:Simplicity: Focus on the essentials. Identify the critical assets and the most likely threats. Implement basic protections, such as strong passwords and regular software updates.
Cloud Considerations: Leverage cloud services for scalability. Ensure proper security configurations and consider third-party security certifications.
Employee Training: Prioritize cybersecurity awareness among employees. Regular training can significantly reduce the risk of human error.
Adapting the Framework for Enterprises
Larger enterprises face complex networks and a higher volume of potential vulnerabilities. Adapting the NIST Framework for enterprises involves:Centralized Management: Implement centralized security management tools for consistent control across diverse systems.
Advanced Monitoring: Invest in advanced threat detection and monitoring tools to identify sophisticated threats in real-time.
Incident Response Teams: Establish dedicated incident response teams and conduct regular drills to ensure a swift and effective response.
Benefits of NIST Cybersecurity Framework
The NIST Cybersecurity Framework offers several significant benefits to organizations that choose to adopt and implement it. These benefits contribute to improved cybersecurity practices, enhanced risk management, and a stronger overall security posture. Here are some of the key benefits of using the NIST Cybersecurity Framework:1. Structured Approach to Risk Management
The framework provides a structured and organized approach to identifying, assessing, and managing cybersecurity risks. It helps organizations prioritize their cybersecurity efforts based on their unique risk profile, enabling them to allocate resources effectively.2. Customizability
The framework is adaptable and can be tailored to the specific needs and characteristics of different organizations, regardless of their size, industry, or cybersecurity maturity level. This allows organizations to implement controls that align with their business objectives and risk tolerance.3. Improved Communication
The framework's standardized terminology and structure facilitate better communication between different stakeholders within an organization. This includes IT teams, management, legal departments, and external partners.4. Enhanced Collaboration
The framework encourages cross-functional collaboration by involving various departments in the cybersecurity risk management process. This collaboration helps break down silos and creates a more cohesive and coordinated cybersecurity strategy.5. Cybersecurity Maturity Evaluation
The framework enables organizations to assess their cybersecurity maturity and progress over time. By evaluating their current state against the framework's recommendations, organizations can identify gaps and areas for improvement.6. Vendor and Partner Alignment
The framework serves as a common language for discussing cybersecurity requirements and expectations with vendors and partners. This helps ensure that third-party products and services align with an organization's cybersecurity goals.7. Guidance for Small Businesses
Small businesses often lack dedicated cybersecurity resources. The framework provides a structured approach that can be scaled down to fit the resources and capabilities of smaller organizations, helping them improve their cybersecurity posture.8. Regulatory and Compliance Alignment
The framework aligns with various industry regulations and standards, making it easier for organizations to demonstrate compliance with cybersecurity requirements.9. Continuous Improvement
The framework promotes a culture of continuous improvement by emphasizing regular assessment, adjustment, and enhancement of cybersecurity practices. This adaptive approach helps organizations stay up to date with evolving cyber threats.10. Risk-Informed Decision Making
Organizations can make informed decisions about cybersecurity investments by focusing resources on areas that address the highest risks. This approach maximizes the impact of cybersecurity efforts.11. Incident Response Preparedness
Implementing the framework's guidelines for incident response planning and communication enhances an organization's ability to effectively respond to and recover from cybersecurity incidents.Conclusion
The NIST Cybersecurity Framework offers a flexible approach that can be tailored to organizations of varying sizes. Whether you're a startup with limited resources or an enterprise managing intricate networks, the NIST Framework provides a roadmap to bolster your cybersecurity defences. By identifying your unique risks, adopting appropriate safeguards, and fostering a culture of cybersecurity, you can leverage the NIST Framework to mitigate threats and protect your organization's digital assets. Remember, cybersecurity is an ongoing journey, and the NIST Framework can be your steadfast guide along the way.To access further insights and assistance regarding this subject, we invite you to explore our official website and feel free to submit your inquiries. Our team is committed to providing comprehensive solutions and is eager to address any challenges you may encounter. Your concerns are of utmost importance to us, and we look forward to assisting you.
Blue Summit has collaborated with OdiTek Solutions, a frontline custom software development company. It is trusted for its high service quality and delivery consistency. Visit our partner's page today and get your business streamlined.
REFER TO OTHER RELEVANT CONTENTS

From Startups to Enterprises: Tailoring the NIST CSF Framework to...
In an era where cyber threats have become more sophisticated and pervasive, organizations of all sizes are realizing the importance of robust cybersecurity measures. The NIST (National Institute of Standards and Technology) Cybersecurity Framework has emerged as a versatile and comprehensive guide to help organizations...
read more








